Overview
The third Silicon Salon, on January 18, 2023, expanded our community of crypto-wallet developers and semiconductor manufacturers to also include the halls of academia.
Once again, the community came together to discuss the requirements and realities of semiconductor design, but this time the focus was on new silicon-logic-based cryptographic functionality as well as new opportunities for semiconductor acceleration, such as Multi-Party Computation (MPC) and ZK-proofs.
“What we’re trying to explore today is silicon logic–based cryptographic functionality. What are the opportunities for semiconductor acceleration of cryptography, as MPC and ZKP technologies are beginning to be deployed?”
Presentations
The third Silicon Salon featured three presentations, from Bunnie Studios and Cramium Labs, as well as cryptographer Kavya Sreedhar. There were also question & answer sessions after each presentation.


Cramium Labs Presentation
View the presentation including video and slides.
Key Slides
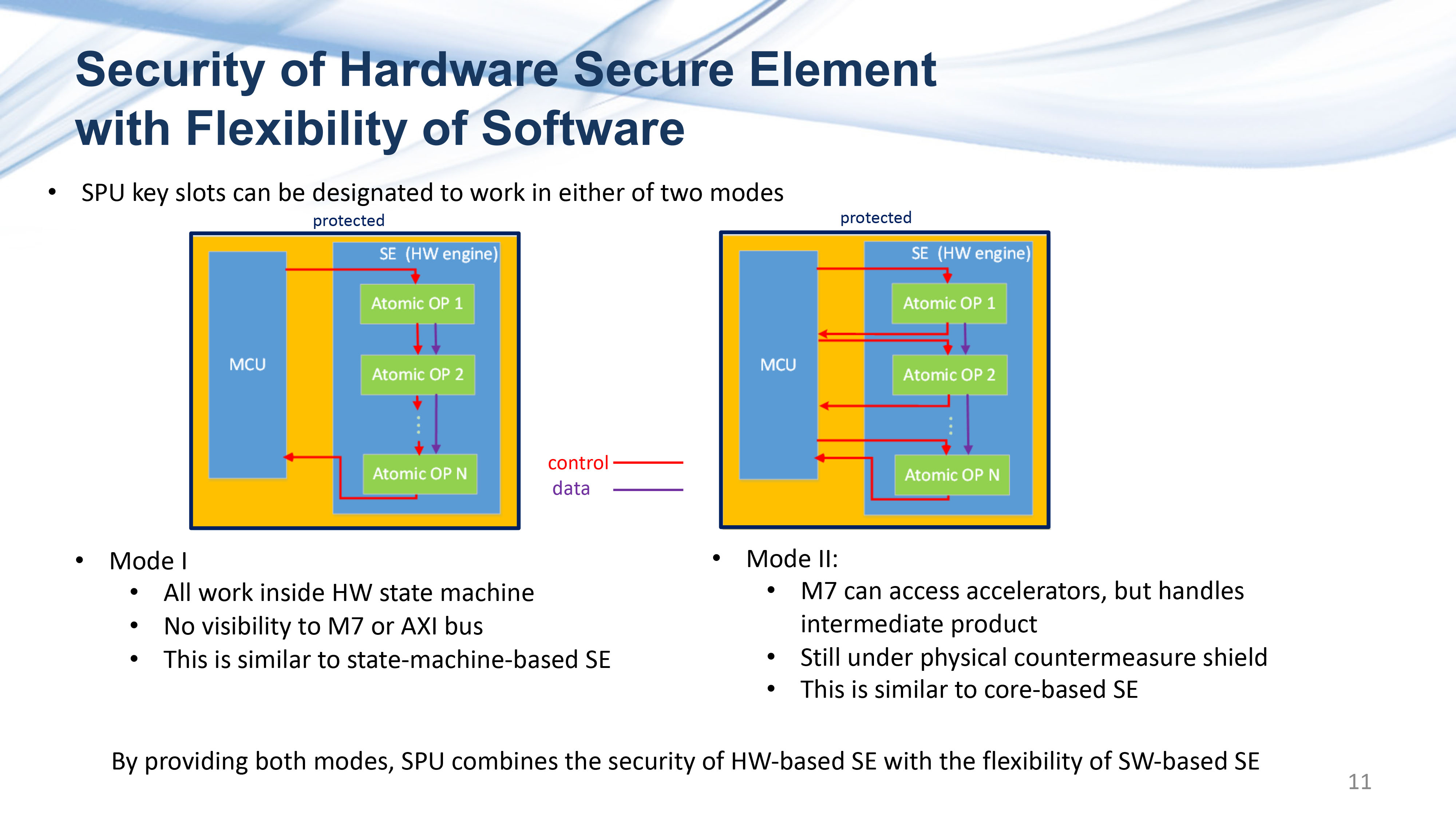
Key Quotes
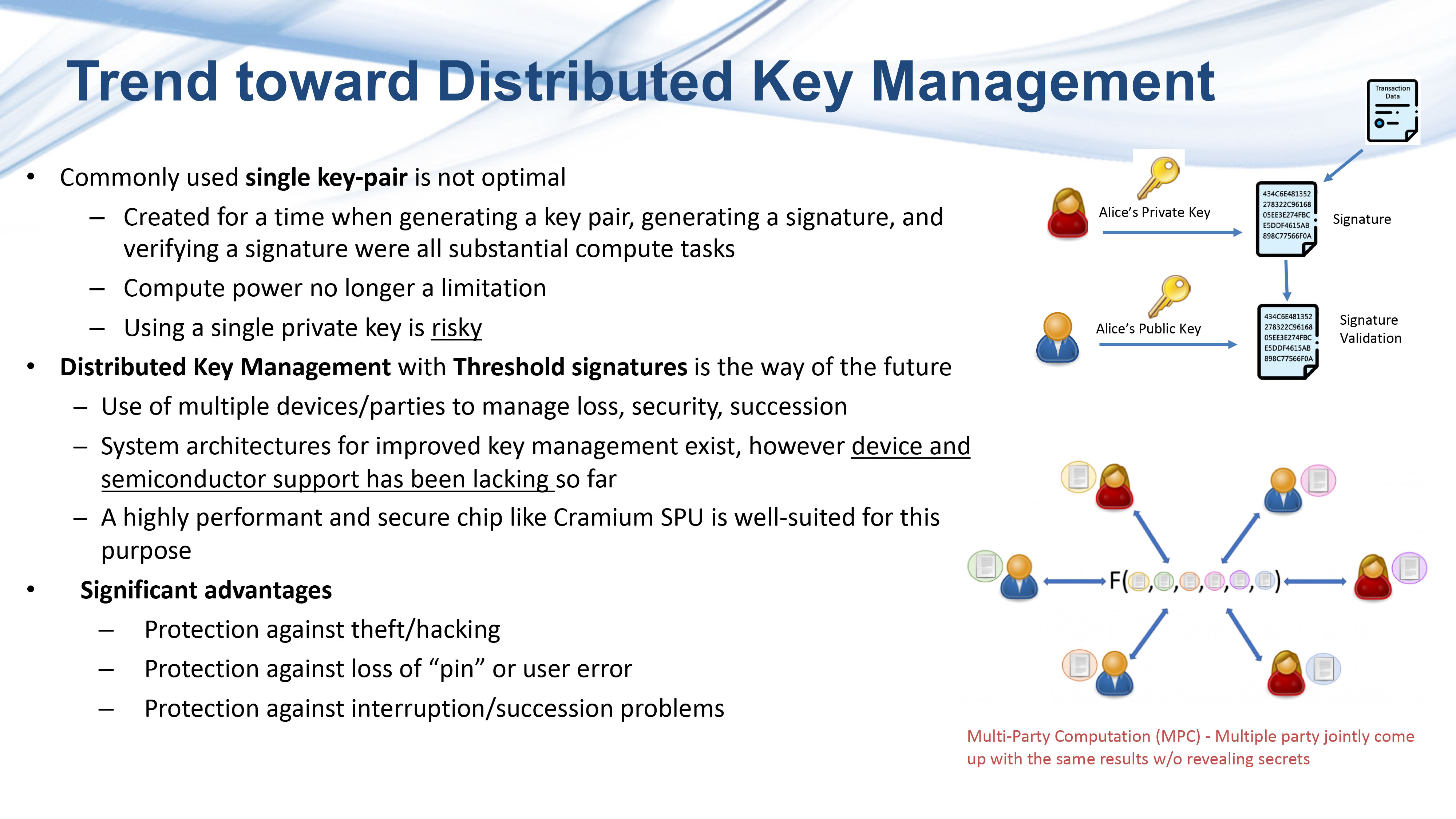
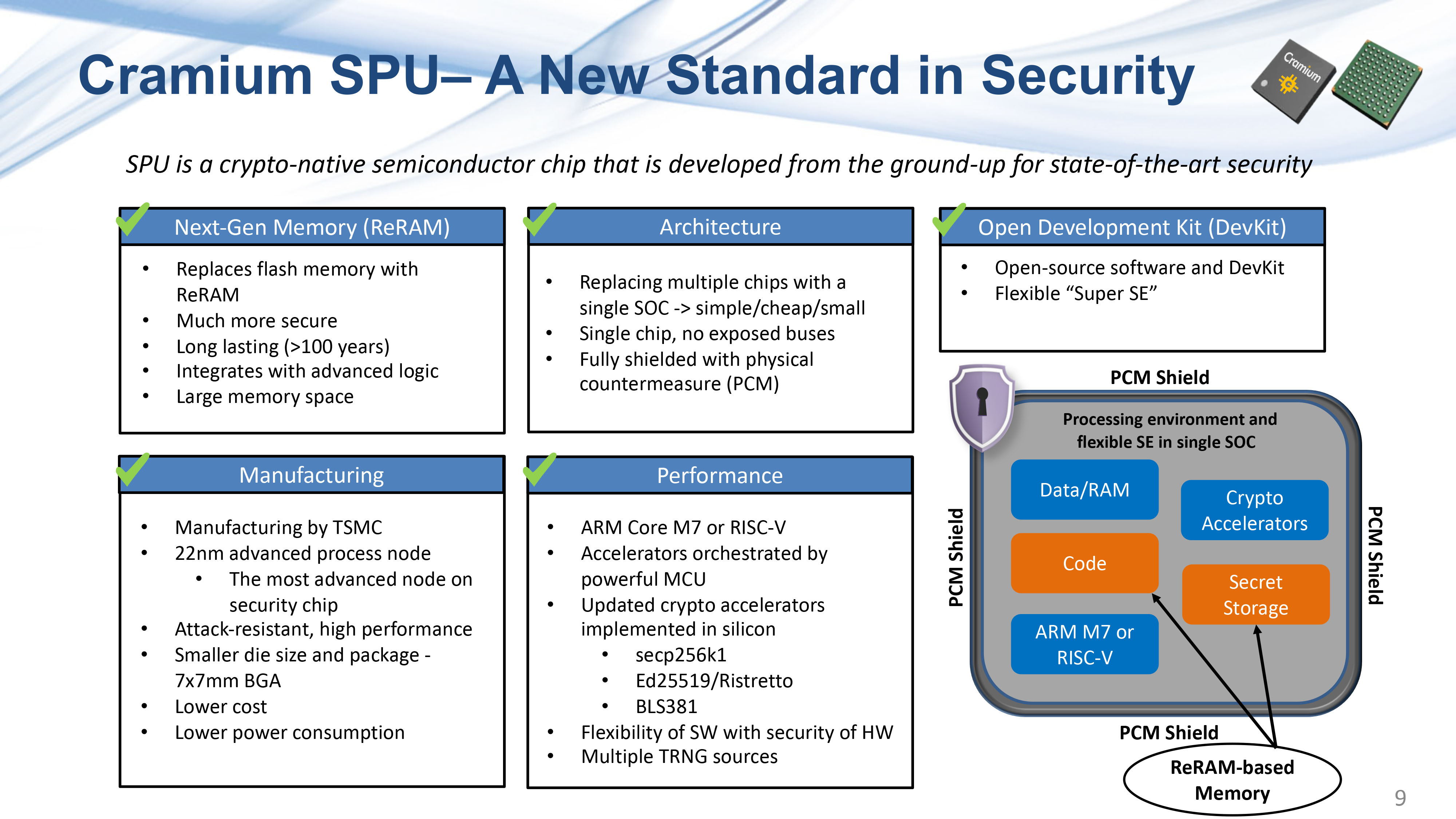
Security: “The single-key scheme has become more risky.”
Support: “Unfortunately there has not been much support from semiconductor manufacturers for MPC and other schemes. We have identified this problem, and Cramium was formed to help solve this challenge.”
Speed: “Key generation here already takes several seconds or even more than 10 seconds. This is one of the reasons why software-only solutions are not good enough.”
Goal: “We aim to provide a flexible and programmable computing platform, and we want to take an open development approach.”
Bunnie Studios Presentation
View the prseentation including video and slides.
Key Slides

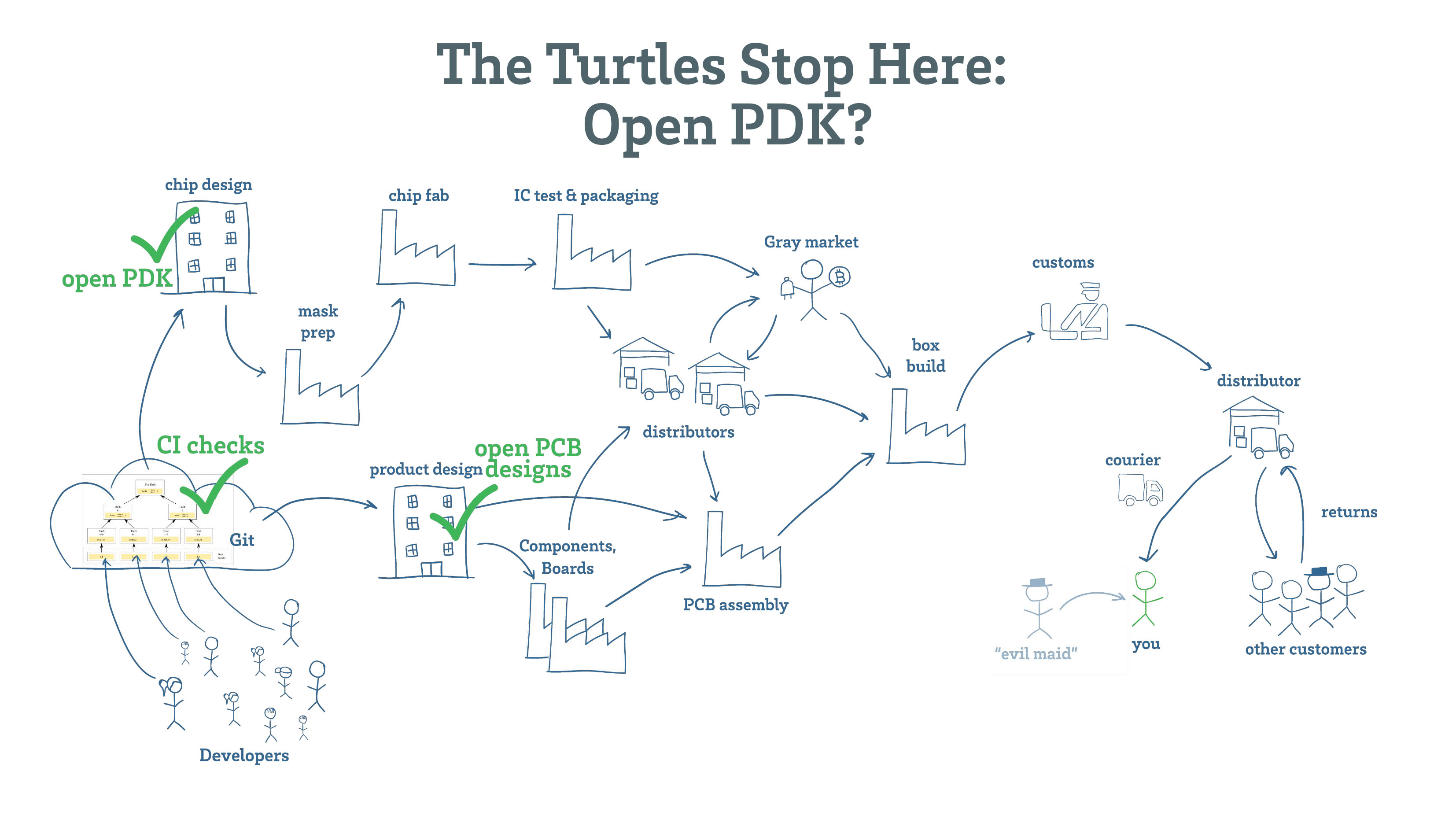

Key Quotes
Foundations: “If you can’t trust the transistors, then why bother with anything else?”
The Nth Turtle: “Let’s have open circuit boards, firmware, bootloader, kernel, protocols, and applications. And also open chips, RTL, PDK, masks, and chip fabs. The problem is that you can keep going down and down and down until you get to the nth turtle.”
Look Closer: “You can always walk around any security countermeasure by going one level deeper and then trapping the upper security level in a state where you are running a simulation and the world is not what it appears.”
Physical Hashes: “There is no ‘hash function’ and ‘digital signature’ for physical hardware. At least not yet.”
Tradeoffs: “Hardware security is a cost-benefit tradeoff at the end of the day, like fatality rates in automobile accidents.”
Kavya Sreedhar Presentation
View the presentation including video and slides.
Key Slides
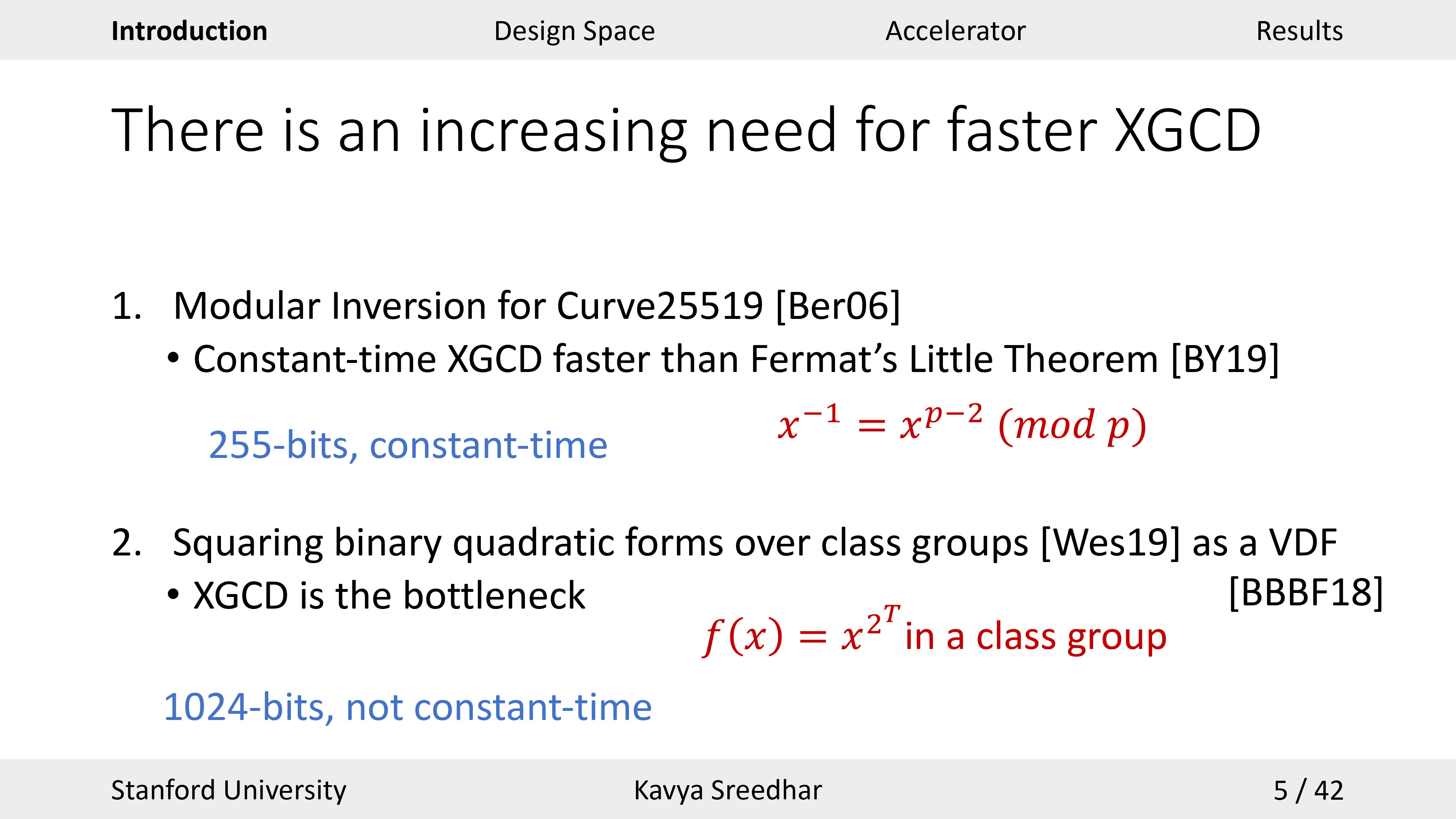
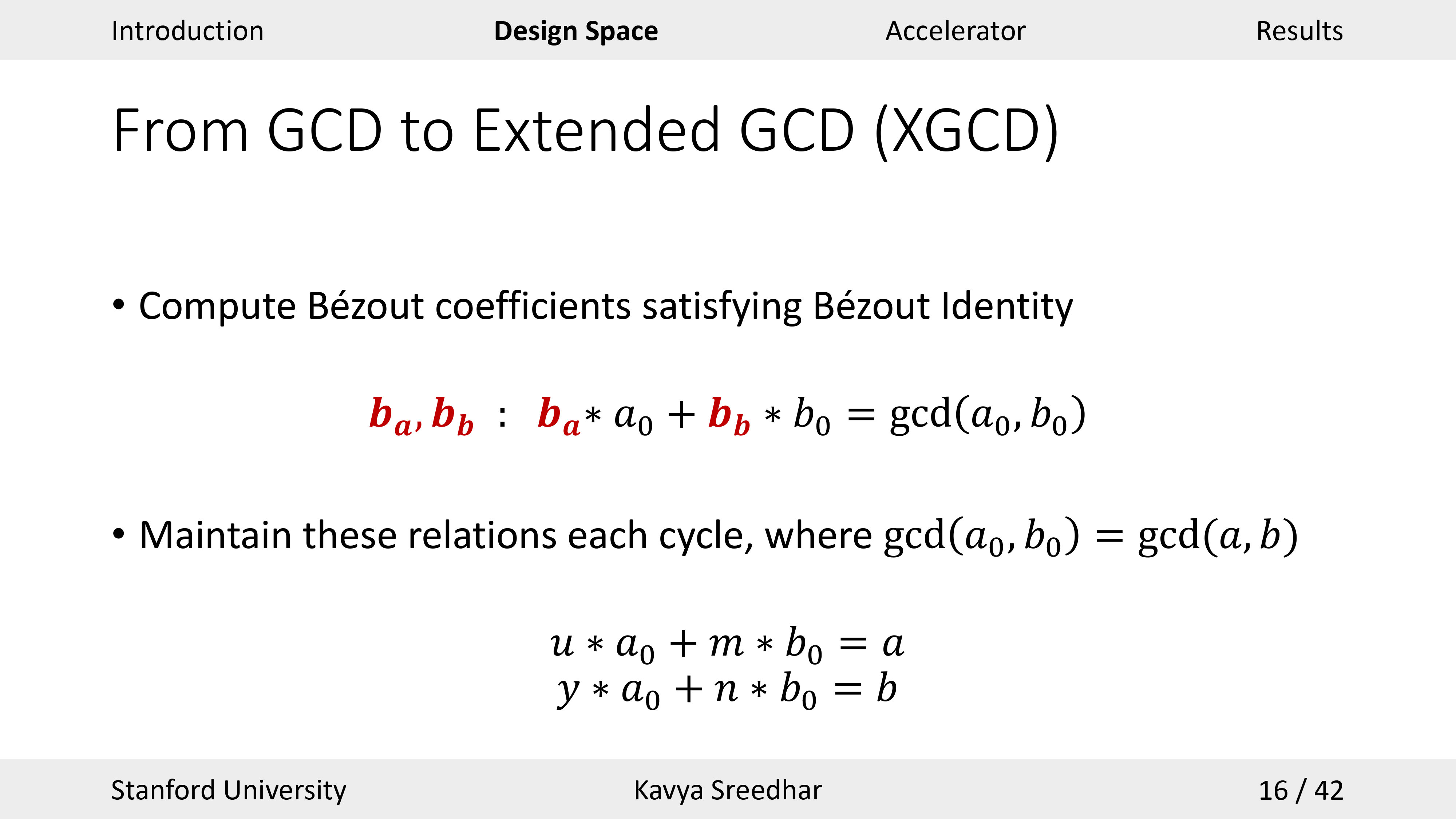
Key Quotes
New Needs: “Recently there has been a larger need for fast extended GCD implementations.”
Goal: “Our goal was to explore the broader design space across different areas, like target platform, algorithm, and application requirements.”
Additional Discussions & Chat
An hour’s worth of additional discussion continued to iterate through some of the topics brought up at Silicon Salon 3.
Key Quotes: Hardware Challenges
“There’s huge barriers to getting an algorithm into a chip.”
“We constantly struggle with a difference in mentality and constraints between software versus chip business.”
“Sounds like we should just stick to doing security in heterogenous hardware using software.”
Key Quotes: Hardware & Standards
“There’s a lot of competing standards with MPC. … [There’s a] strong need for standardizing.”
“Without having standardization, the answer is probably to implement as many things as you can.”
Key Quotes: Distributed Key Generation
“Distributed Key Generation is one of the best answers out there. Rather than worrying about your entropy, you just collect as much entropy as you can from as many parties as you can and that is your key generation.”
“We’re kind of moving the secrets to a new place, and the damage they can do is reduced on an individual loss basis, but it’s still a secret that requires some level of care.”
“I know of dozens of MPC protocols, with different assumptions and cryptographic primitives. IMHO the field needs a strong effort to standardize in order to identify which primitives should be implemented in silicon. There are just too many of them right now and many of them are grad-student-ware.”
Key Quotes: Collaboration
“We get to share a little bit about what we’ve been thinking about from the hardwaree perspective and importantly get to learn about what you all are thinking about from the cryptography application perspective, and that really informs what we’re looking at next and how we can be helpful given our backgrounds.
“This connection to being aware of what are the interesting problems and what’s currently going on, that matters a lot!”
“Thank you for listening to have what we have to save and sharing your knowledge with us.”
Possible Future Discussions
Suggestions for future Silicon Salons include supply chain, standardization, and hardware open development.
Participants
Thanks to our presenters and other participants!
- Host: Blockchain Commons
- Facilitators: Christopher Allen, Bryan Bishop
- Presenters: Bunnie Studios, Cramium Labs, Kavya Sreedhar
- Sustaining Sponsors: Bitmark, Chia, CrossBar, Foundation, Proxy, Unchained Capital
Chatham House Rules Apply
The Silicon Salon occured under the Chatham House Rules, meaning that information could be freely used by all participants and statements could be quoted, but not attributed. A goal of Blockchain Commons is to give principals in the Web3 and blockchain space the ability to discuss potential interoperability, but to do so in a safe way.
Silicon background image courtesy of Vecteezy.
